At 2:30pm today I received a Facebook update from my Intelligist Group partner, Alan Berkson:
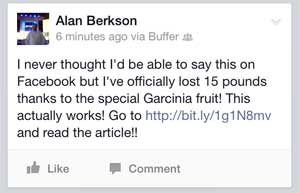
I know him. Well. As funny as it was, it’s not his humor. A quick glance at the source of the post was all I needed to know. He’d been hacked. More accurately, Buffer had been hacked.
Buffer is a common – and free – application (bufferapp.com) that allows you to share content with others. It’s a time-saving tool that’s super easy to use. Download the app and connect it to your social accounts. See something cool on the web that you’d like to curate for others? Use your Buffer app to share it then or later (hence the name Buffer) to your contacts on LinkedIn, Facebook, Twitter and App.net (yes, I know, App.who?).
It’s a brilliant app that saves time and makes you look like a curation monkey.
I use it. Daily. Along with thousands of other people. No, make that a million other people. Not impressed by a million users? How about the fact that they nailed 50,000 users in their first 8 months of operation?
And that’s the problem. Like many users, I don’t often give a second thought to who’s behind an app. If it’s available on the Google and Apple stores, it’s fine by me. Not any longer.
Designing apps is easy. If I can do it, I assure you anybody can. Developing and implementing? A bit more difficult, but still relatively easy. Making money off your app? That’s a bit of a challenge.
But consider this…
We live in a world were apps are increasingly easy to develop. The cost of entry is often less than a few thousand dollars (if that).
Now consider how often – without a second thought – we use the authentication features to allow apps to post on our behalf… to have access to our contacts… to tell us how high our social influence score is… to have access to all of our social data…
We do it all the time. Every day. All because we have some misconstrued feeling of trust in an app vendor we probably know very little about.
If you haven’t thought about how easy it is to build an app with the end goal of “hacking itself” for ill-gotten gain, of leveraging all of your contact and social data for purposes other than posting an update, etc. you should. Not every form of monetization is legit.
Look how easy it was for Buffer (which has access to Twitter, LinkedIn, Facebook, etc.) to get hacked.
Imagine if somebody actually built an app with the sole purpose of leveraging it for hacks – hacks that you’ll probably not even notice.
#justsayin